
Thank you! Your submission has been received!
Oops! Something went wrong while submitting the form.


March 12, 2025
First National Calls: 50 selected projects to start in 2025
First National Calls: 50 selected projects to start in 2025
50 proposals were selected through the review processes of the SDSC's first National Calls.
Blog

January 22, 2025
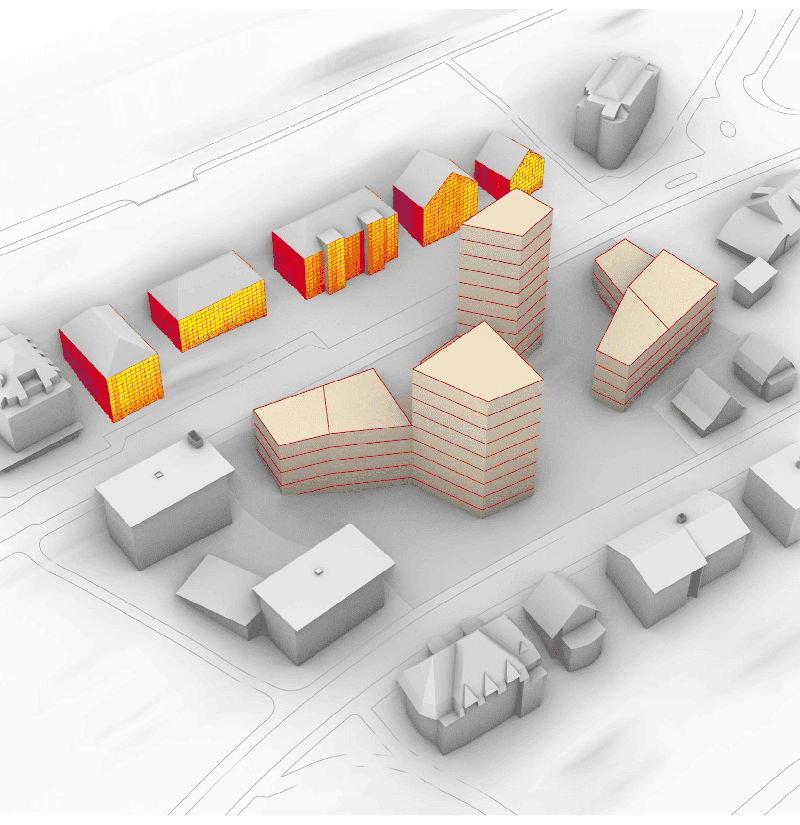
AIXD | Generative AI toolbox for architects and engineers
AIXD | Generative AI toolbox for architects and engineers
Introducing AIXD (AI-eXtended Design), a toolbox for forward and inverse modeling for exhaustive design exploration.
Blog


May 1, 2024
Smartair | An active learning algorithm for real-time acquisition and regression of flow field data
Smartair | An active learning algorithm for real-time acquisition and regression of flow field data
We’ve developed a smart solution for wind tunnel testing that learns as it works, providing accurate results faster. It provides an accurate mean flow field and turbulence field reconstruction while shortening the sampling time.
Blog


April 22, 2024
The Promise of AI in Pharmaceutical Manufacturing
The Promise of AI in Pharmaceutical Manufacturing
Innovation in pharmaceutical manufacturing raises key questions: How will AI change our operations? What does this mean for the skills of our workforce? How will it reshape our collaborative efforts? And crucially, how can we fully leverage these changes?
Blog

March 20, 2024
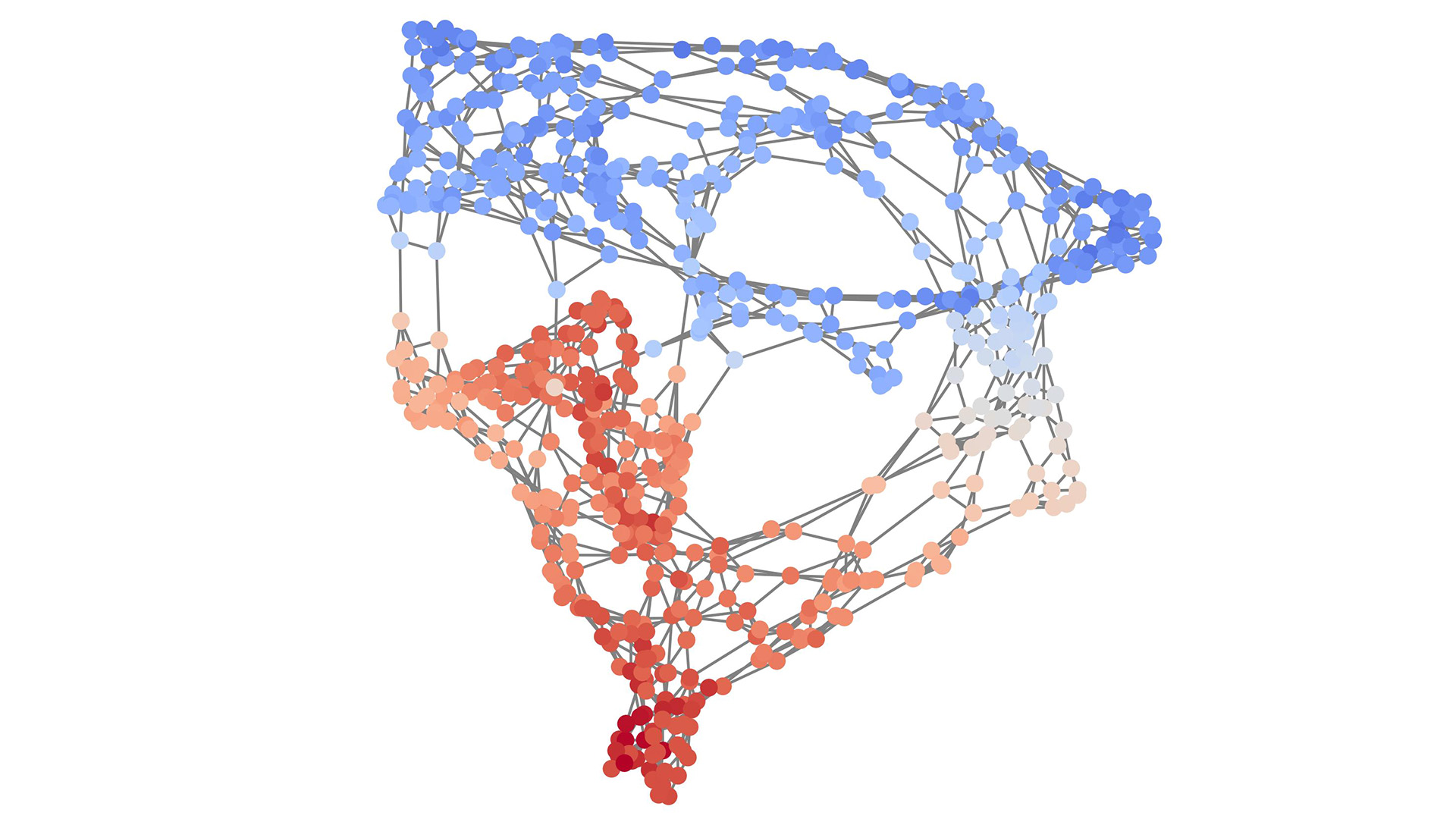
Efficient and scalable graph generation through iterative local expansion
Efficient and scalable graph generation through iterative local expansion
Have you ever considered the complexity of generating large-scale, intricate graphs akin to those that represent the vast relational structures of our world? Our research introduces a pioneering approach to graph generation that tackles the scalability and complexity of creating such expansive, real-world graphs.
Blog


March 6, 2024
RAvaFcast | Automating regional avalanche danger prediction in Switzerland
RAvaFcast | Automating regional avalanche danger prediction in Switzerland
RAvaFcast is a data-driven model pipeline developed for automated regional avalanche danger forecasting in Switzerland.
Blog
Contact us
Let’s talk Data Science
Do you need our services or expertise?
Contact us for your next Data Science project!
